How to Find Vulnerabilities for Any Website Using Nikto?

There are a number of tools and applications to find vulnerabilities in websites, but one of the simplest (and one of my favorites) is nikto.
This small and simple tool examines a website and reports back to you the potential vulnerabilities that it found that you could use to exploit or hack the site. In addition, it’s one of the most widely used website vulnerabilities tools in the industry and in many circles considered the industry standard.
Although this tool is extremely useful and effective, it is NOT stealthy. Any website with an IDS or other security measures in place will detect that you are scanning it. Originally designed for security testing, it was never meant to be stealthy.
Step 1Fire Up Kali & Open Nikto
Let’s fire up Kali and get started with nikto. Once we have Kali up and running, go to Kali Linux -> Vulnerability Analysis -> Misc Scanners -> nikto, like in the screenshot below.- nikto -h <IP or hostname>
Step 2Scan the Web Server
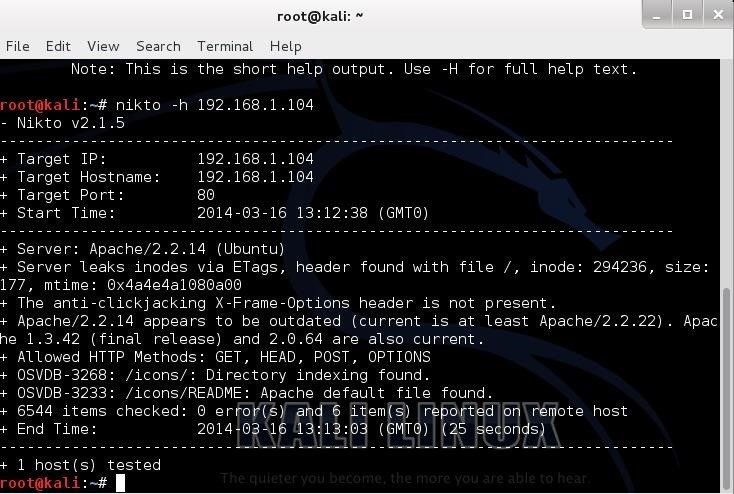
Let’s start with a safe web server on our own network. In this case, I have started the http service on another machine on my network. There is not a website hosted by this machine, just the web server. Let’s scan it for vulnerabilities by typing:- nikto -h 192.168.1.104
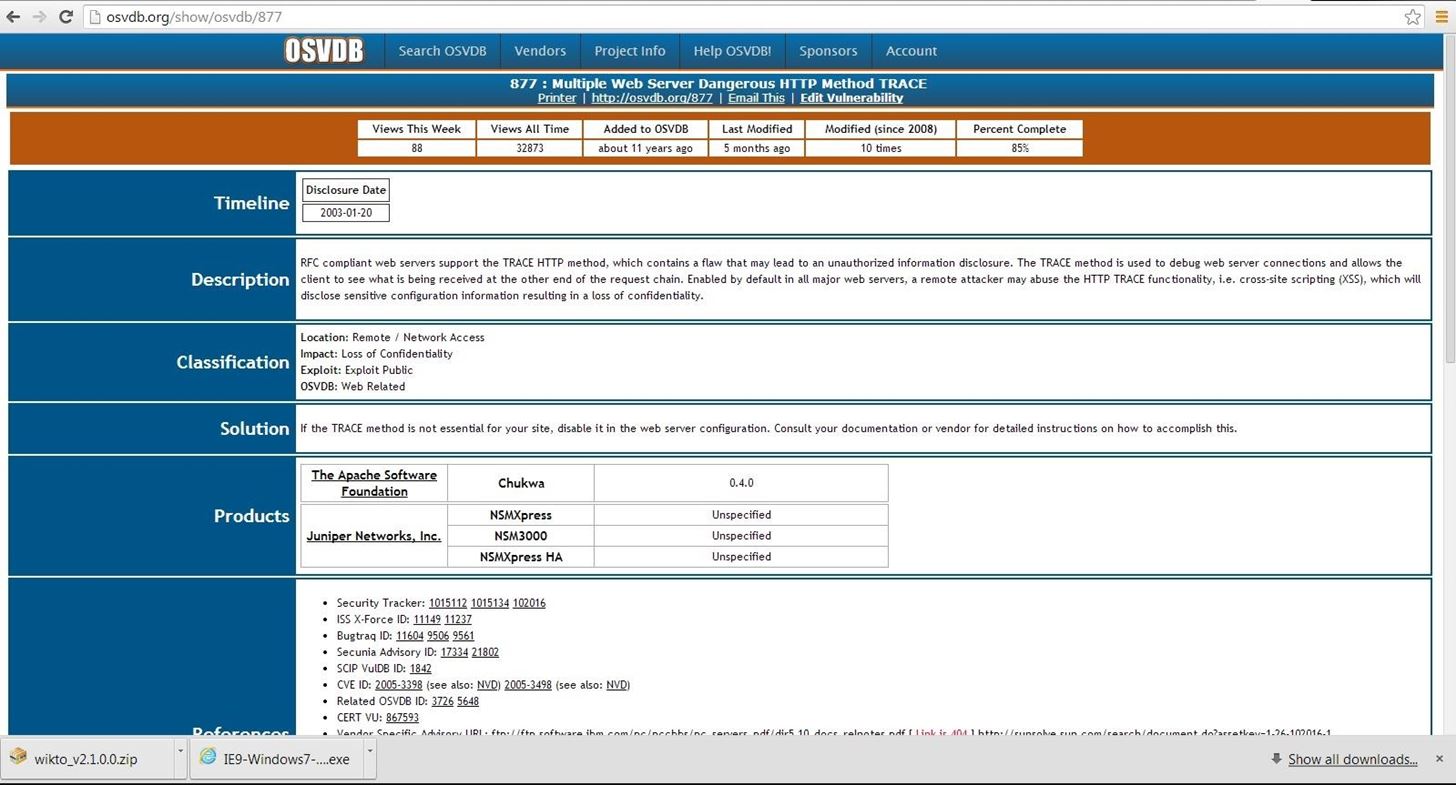
Note near the bottom that it identifies some vulnerabilities with the OSVDB prefix. This is the Open Source Vulnerability Database. This is a database maintained of known vulnerabilities at http://www.osvdb.org, in addition to other databases I covered, such as SecurityFocus and Microsoft’s Technet.
Step 3Scan the Site
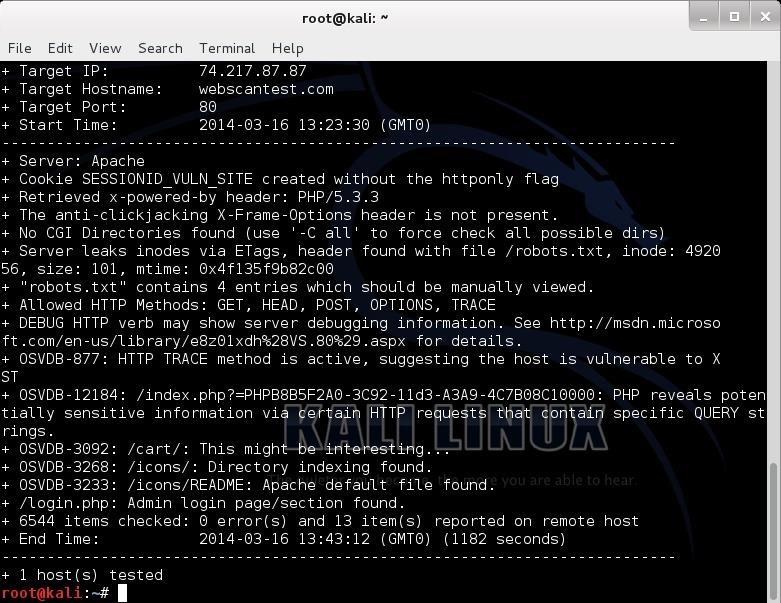
Let’s try another site. In an earlier tutorial, we had hacked a web server named webscantest.com. Let’s see what nikto can tell us about this site.- nikto -h webscantest.com
Scan WonderHowTo
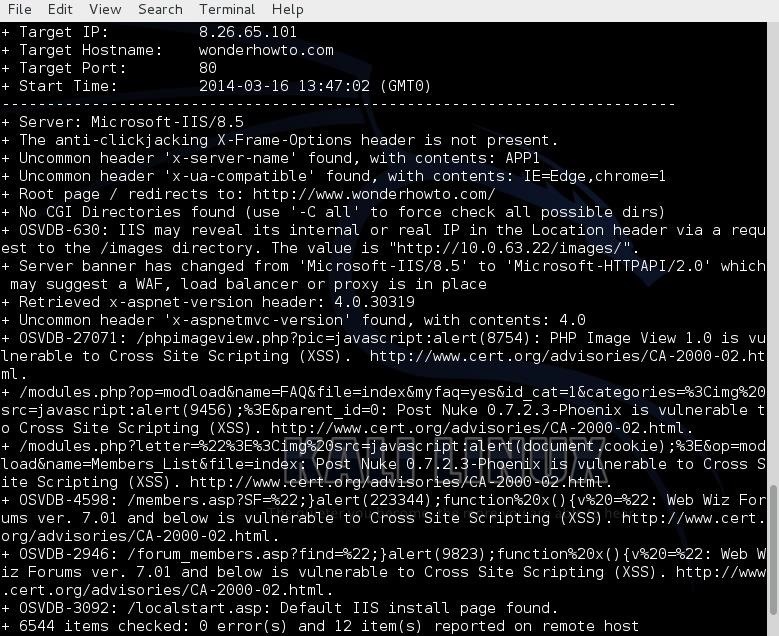
Let’s scan a few more sites and see what it can tell us about these sites. Let’s see what we can find out about our own website, www.wonderhowto.com.- nikto -h wonderhowto.com
False positives like this can appear because the scan does not actually execute each of the possible vulnerabilities, but rather scans to see if the server responds without error to known exploitable URLs.
Scan Facebook
Finally, lets point nikto at www.facebook.com.- nikto -h facebook.com
thnks


Comments
Post a Comment